
What is SSL?
SSL or Secure Sockets Layer is a networking protocol that is designed for securing the connections between web clients and web servers on an insecure network, like the Internet. SSL has made it possible for the web servers in order to enable a secured online transaction between the consumers and businesses. Due to a number of protocols and flaws in its implementations along with vulnerabilities, SSL has been depreciated for its usage on the Internet and in the year 2015, SSL certificates were replaced by the Transport Layer Security (TLS) protocol.
Role of SSL
SSL mostly uses as a protocol for securing the online transactions and with time, it eventually was used for a secured authentication and encryption for other applications present at the network transport layer. SSL uses a combination of public and private key encryption along with other cryptographic functions for securing a connection between the two machines. These machines usually include- either a web server or a mail server and a client system, that establishes the communication between them over the Internet or another TCP/IP network.
SSL is meant for providing a mechanism for encrypting and authenticating data that is sent between the processes running on the systems of client and server. SSL is also used for mediating the secured exchange of private keys for session encryption by the means of SSL certificate issued by a trusted certificate authority.
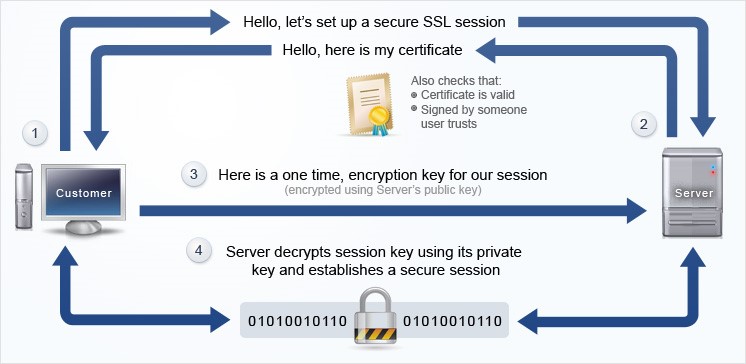
How SSL Works?
The SSL protocol comprises of two sub-protocols, namely- the record protocol and the handshake protocol.
The handshake protocol is responsible for defining how the web client and web server look to establish an SSL connection, inclusive of the negotiation of the cryptographic systems that each host either ready or not to use for communication. SSL also mentions the processes for exchanging cryptographic material like the SSL certificate for authenticating web servers, public keys for authenticated transmission of data and private keys for session encryption.
The record protocol depicts how the hosts communicate with each other for exchanging data using the SSL. It also includes the specifications for how data needs to be prepared for transmission and how it would be verified/decrypted upon arrival at the recipient end.
What is Certificate Authority?
A certificate authority or CA depicts a trusted body that is responsible for issuing digital certificates. The digital certificates are data files that are used for cryptographically linking an online entity with public keys. The certificate authorities are now becoming an essential part of the Internet’s public key infrastructure (PKI) as they are the authoritative body that issues SSL certificates that are used by web browsers for authenticating content sent from web servers.
The root certificate of the certificate authority should not be used directly for signing the digital certificates. Rather it should be used for generating the intermediate certificates as required; considering different intermediate certificates are generated for different purposes. The certificate authorities can accept the requests coming from the applicants directly. They often are responsible for delegating the task of authenticating applicants to the registration authorities (RAs). Registration authorities are often used for purposes of marketing and customer support. RA can collect and authenticate the digital certificate requests, and then submitting those requests to the CA. The CA then issues the certificate that has to be passed through the RA to the certificate requestor.
Uses of Certificate Authority
Probably, the best-known use of a certificate authority is to issue the SSL certificates to all those who’re publishing content on the Internet. The certificate authorities issue 3-levels of SSL certificate and corresponding to a different level fo trust through these certificates. Certificates that ensure higher trust levels tend to cost more as they need more operations on the certificate authority part.
Following are the three different levels of trusted certificates-
Extended Validation (EV):
These certificates are meant to provide the highest assurance level validated by the certificate authority to the entity that has requested for the certificate. The Certification Authority Browser Form explains the detailed requirements for the process that the certificate authorities need to apply when they verify the information that is provided by the applicant asking for an EV certificate.
Organization Validated (OV):
These certificates provide higher level of assurance. The certificate authorities usually perform some kind of screening of the certificate applications and it may include telephonic verification or even use of external or third parties for confirming the information that is submitted by the applicants. OV certificates are issued only if the applicant can demonstrate his administrative control of the domain for which he has requested the certificate. Also, the organization needs to be shown as a legal existing entity.
Domain Validated (DV):
These certificates just require the applicant to show his ownership for the requested domain. DV certificates can be gained instantly and at a low cost.
Besides issuing SSL certificates related to the domain name, a certificate authority can issue other types of digital certificates. The certificate authorities in recent times have changed their focus from just issuing SSL certificates for web domains to a wider range of certification services.
SSL Certificate for Small Businesses
It doesn’t really matter whether a business has just started or is an established firm in the industry. Web security remains a major concern and it should not be undervalued at any cost. Hacking attempts are going up at a significant and alarming rate. For hackers, small businesses can become an easy target, as the small businesses don’t emphasize too much on their web security and also lack funds that are needed for huge security implementations. A fact states that nearly 43% of the cyber-attacks that occur, the targets are small businesses only. Another fact states that 60% of the small businesses are forced to shut down within 6 months of their existence due to cyber-attacks.
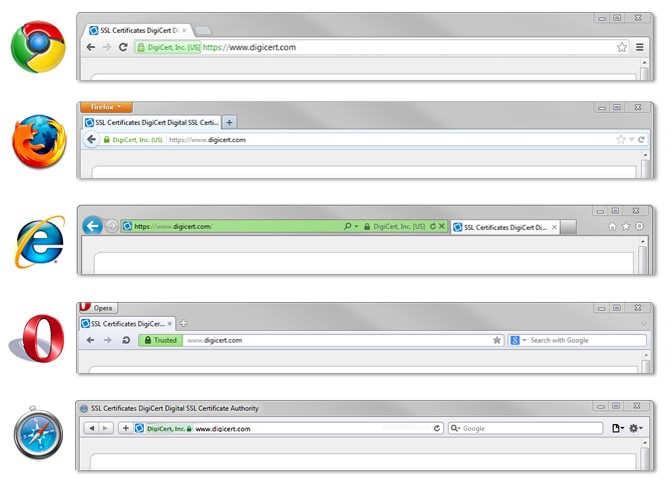
The people usually are reluctant to trust any small businesses, and the fact is the recall of a small business is very difficult. Thus, it becomes quite essential for small businesses to establish a trust foundation with their potential customers. Security has always remained a major concern for online users. The customers have the habit of abandoning their purchases if they find that the site is not secured enough and there are high chances of visitors not returning to the unsecured pages of small business. When the small business sites have an SSL certificate installed on their site, then their website is equipped with certain visual indicators like a green address bar or a green padlock. When the visitors notice these visual indicators, then the conversion rate on the website is bound to rise up and as a result of this small businesses can generate huge revenue.

